An offline, cold storage Bitcoin or crypto wallet is a major step in upgrading your cryptocurrency security.
Cold storage wallets keep your Bitcoins offline, and away from online computers where hackers would be able to access and steal them.
Hardware wallets are the most common form of cold storage today.
Why?
They offer the best security per dollar spent and are very good at preventing you, the user, from making mistakes that can lose all of your Bitcoins.
More bitcoins are lost due to users making mistakes than from hackers.
 Ledger Nano X
Ledger Nano X Price: $166
Release Date: May 15th, 2019
There is a reason Ledger is the largest hardware wallet manufacturer in the world. Their wallets are simple to set-up, easy to use, and have a very strong security record. Their main downsides are their non-ergonomic design, and some complain of Ledger's recent change in direction as a company.

-
 Trezor Model T
Trezor Model T Price: $219
Release Date: October 31, 2017
If you are looking for a hardware wallet with a big screen that is very easy to navigate, then the Trezor Model T is the hardware wallet for you. If you want a wallet from the original inventor of the hardware wallet, then all the more reason to Grab a Trezor Model T. This is an expensive wallet though, and because of some design choices Trezor made early on, it is NOT the most secure if someone physically gets their hands on it and they know what they are doing.

-
 Coldcard Mk 4
Coldcard Mk 4 Price: $148
Release Date: March, 2023
The Coldcard MK 4 is Coinkite's latest version of their hardware wallet models. Like the Passport, this is also an advanced wallet with lots of features to make the kinds of bitcoin transactions you want!

-
 Foundation Passport
Foundation Passport Price: $199
Release Date: March 31, 2021
If security is your number one priority in a wallet, some would say you can't do better than Foundation Device's Passport hardware wallet. It's unassuming look of a mobile phone, air-gap features, and multiple security validation checkpoints make this a holder's security dream.

-
 Ledger Nano S Plus
Ledger Nano S Plus Price: $79
Release Date: April 4th, 2022
Ledger also gets awarded "best value" hardware wallet with its newest addition to the Nano family of hard ware wallets. For a mere $88, you get basically all of the features of the Nano X, just without any Bluetooth capabilities and a slightly lower resolution screen.

-
| Nano X | Passport | Coldcard Mk 4 | Trezor Model T | Nano S Plus | |
|---|---|---|---|---|---|
| Price | $166 | $199 | $148 | $219 | $88 |
| Screen Res. | 128x64 LCD | High-Rez Color IPS | 128x64 LCD | 240x240 Color Touch LCD | 128x64 LCD |
| Secure Elements | 1 | 1 | 2 | 0 | 1 |
| Battery | 8 hours | None | None | None | None |
| Storage Size | 2MB | Variable | 512kB | Variable | 1.5MB |
| Bluetooth Connection | Yes | No | No | No | No |
| NFC Connection | No | No | Yes | No | No |
| Coin Support | 5500 | Bitcoin Only | Bitcoin Only | 1450 | 5000 |
| PSBT Support | Yes | Yes | Yes | Yes | Yes |
| Camera | No | Yes | No | No | No |
| Open Source Code | No | Yes | Yes | Yes | No |
A hot Bitcoin wallet refers to any wallet that requires the internet to function properly. Hot wallets derive their name from the fact that they need electricity to work.
A cold wallet means your wallet is stored offline and on a device that’s not connected to the internet. “Cold” is a reference to the device being offline.
There are four main types of cold storage wallets:
Hardware wallets are little mini computers that store your Bitcoin offline.
A steel wallet is a piece of nearly indestructible stainless steel that you can use to carry your bitcoin private keys or backups.
You do this by etching or tiling the words into the steel.
This makes it an excellent choice if you are:
Steel wallets are interesting because they can act as both a “paper wallet” or as a backup for any kind of Bitcoin wallet in case yours is lost, stolen, or destroyed.
Almost any crypto holder can benefit from one of these steel wallets regardless of how they choose to store their coins.
If you’re concerned about malicious computer hackers getting access to your wallet, then a paper wallet is one of your best options.

Setting up a paper wallet is for HIGHLY advanced users only. There are many ways to get a paper wallet wrong - all of which can result in a total loss of funds. Proceed at your own risk.
The main drawback of a paper wallet is that it’s extremely prone to damage. If it’s burned, your coins are gone. An upgrade to a paper wallet would to at least be to store in a fire and flood-proof safe or case.
Paper wallets don’t have support teams like hardware wallets. If you get stuck, you’ll have to figure it out on your own using the internet.
As the world’s first bitcoin credit stick, the OpenDime device lets you spend your bitcoin balance in the same way that you would use a traditional credit card.
Here are some pictures I took of my old OpenDimes that I bought to test:

The main difference between OpenDimes and other wallets is that OpenDime only has one address. It’s not a full-fledged hardware wallet that can generate and sign transactions.
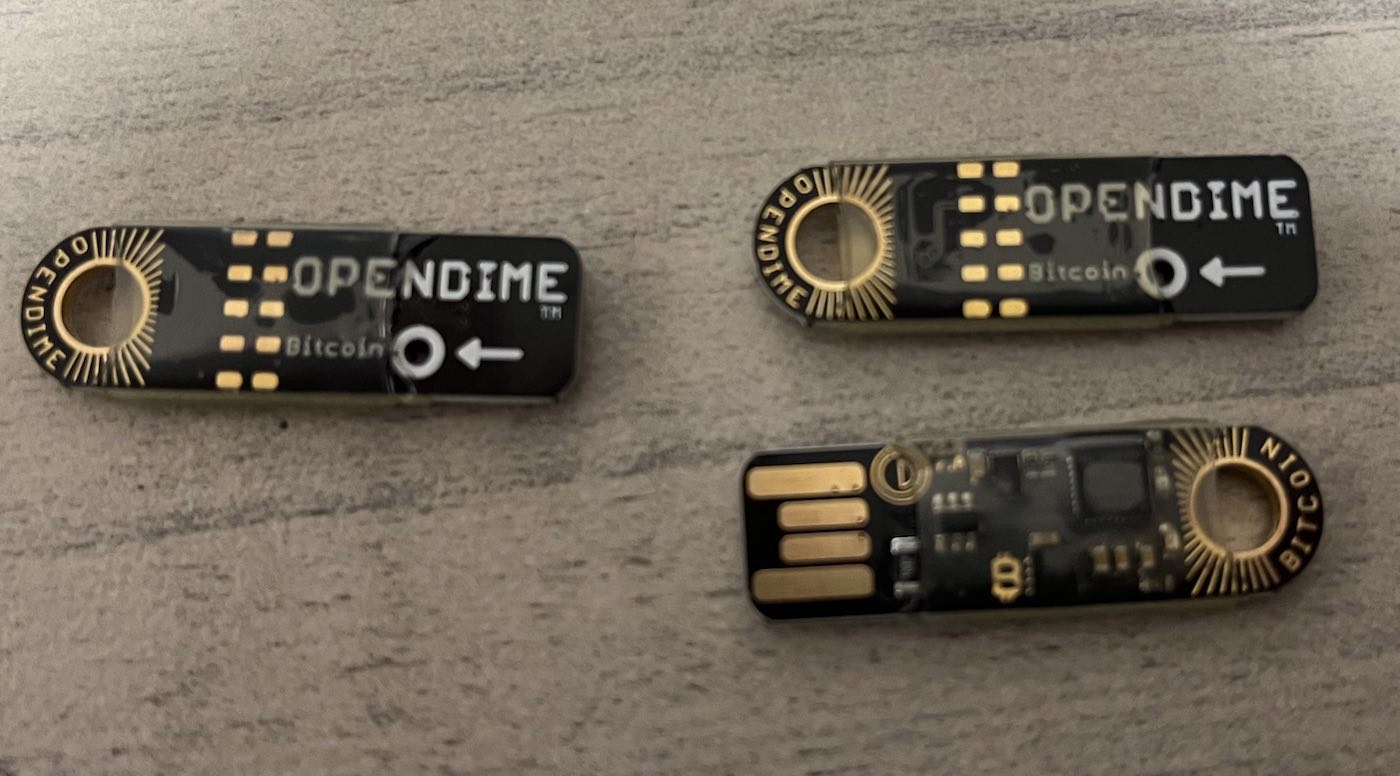
The open dime is very much like a Bitcoin piggy bank.
You can add as much bitcoin to it as you want and as many times as you want, however you can only spend from it once.
At that point, the private key is exposed and the funds are no longer safe on the hardware.
Because of this, its best to send all the coins to a new address once you are ready to use them.

Long-Term Investors: Those who buy and hold cryptocurrencies for extended periods benefit from cold wallets because they prioritize security over frequent transactions.
High-Value Portfolio Holders: People with significant cryptocurrency investments will prefer the air-gapped security offered by cold wallets to protect substantial assets.
Privacy Advocates: Users who value privacy and want full custody of their funds without third-party interference.
Diversified Portfolio Owners: Individuals owning a range of cryptocurrencies, including NFTs and various tokens, might prefer cold wallets that support multiple assets.
However, active traders or those frequently engaging in crypto transactions might find cold wallets cumbersome and might prefer the convenience of hot wallets.
In general, “cold storage” refers to any bitcoin storage storage device that does not require an internet connection.
A cold storage device can be:
In contrast to hot storage, cold storage provides:
If Sony went out of business tomorrow, you would still be able to play your PlayStation with mostly no issues.
Offline crypto wallets are the same. You do not need a company to remain in business in order to continue using your hardware wallet.
Let’s say you use TREZOR with TREZOR’s myTREZOR wallet. TREZOR Wallet goes out of business and no longer supports myTREZOR wallet and it gets shut down.
You could, in just a few minutes, download Electrum on your computer. Once installed, you’d setup your TREZOR and all of your transaction history and balance would get imported and be exactly the same. This is because Electrum will use the same 24-word seed you generated with TREZOR or Ledger on setup.
Cold Storage: Safeguarding Bitcoin by keeping its private keys offline, eliminating online hacking risks.
Deep Cold Storage: An enhanced form of cold storage with added layers of protection.
Cold Storage Methods:
Deep Cold Storage Methods:
Cold Storage Purpose: Protects Bitcoin from basic online threats.
Deep Cold Storage Purpose: Provides the utmost security available, ideal for substantial Bitcoin holdings.
In essence, while both methods aim to secure Bitcoin, deep cold storage offers additional layers of safeguarding against potential threats.
Whether you need deep cold storage or normal cold storage will depend on your holdings.
We didn’t include KeepKey on our list. While it used to be one of the more popular offline wallets, it’s not being updated frequently.
We also did not include Ledger Stax, as it is not available to purchase yet.
There are also a number of hardware wallets that are not open source, so we didn’t include them.
There is one main downside of cold storage and offline wallets:
It can be complicated to access your funds.
Since cold storage wallets are secure, they are harder to access.
If you want to get your money off the wallet, it can be a time consuming task. This is really a pro, because only by adding this time can you get the extra security.
The recovery process for cold wallets will differ depending on the type of cold wallet.
Paper Wallets: For a paper wallet, if it’s a single key wallet, you can just scan the private key with a mobile wallet or a desktop wallet like Electrum.
Hardware Wallets: For a hardware wallet, there are a few ways you can recover your wallet. First is to import the seed into a different hardware wallet. Alternatively, you can use Electrum to restore any BIP39 wallet. Electrum is free for download on Mac and PC.
Steel Wallets: Steel wallets are usually used to store the seed phrase of a hardware wallet. You’ll need to import your steel wallet recovery phrase into one of the programs mentioned above.
BuyBitcoinWorldwide is dedicated to providing readers with detailed and comprehensive reviews. To list the best Bitcoin cold and offline wallets on this page, we researched wallets across the market. Our goal is to make it easy to make informed decisions about cold and offline wallets wallets.
BuyBitcoinWorldWide writers are subject-matter experts and base their articles on firsthand information, like interviews with experts, white papers or original studies and experience. We also use trusted research and studies from other well-known sources. You can learn more about our editorial guidelines.